What’s the deal? I’m testing using https://coveryourtracks.eff.org/ Is it truly unique (and repeatable), or is it perhaps being randomized on every request?
I’ve tried normal Firefox, Mull, and IronFox. With and without jShelter.
I’m using my phone. Stock Android on a Pixel 7 Pro.
In DDG Browser I have a “nearly unique” fingerprint.
I installed CanvasBlocker and disabled privacy.resistFingerprinting in IronFox (since CanvasBlocker said to), and my fingerprint is still unique. I guess I’m not surprised since I think CanvasBlocker is designed to randomize canvas fingerprinting.
Any tips on having even a shred of privacy when browsing the web on Android?
#Update
The biggest identifying characteristics are screen size and user agent. User agent can be faked with an extension. I can’t exactly change my screen size.
I don’t know what exactly what I did, but I managed to improve to “nearly unique” in IronFox. I think all I did was install Cookie Autodelete. It’s an extension I’ve used for a long time in Mull, and finally got around to installing it. Then I installed “User-agent Switcher” and chose a Chrome user-agent and now I’m back to “Unique”. 🤔
EFF mentioned Tor Browser having some other best anti-fingerprinting, so I tried installing that. “Unique Fingerprint”. Again, maybe that’s fine if it means it’s randomized on every request. Does anyone know if that’s the case? If part of the fingerprint is a hash of canvas data and WebGL data, etc. Then I can easily see your fingerprint being unique if a browser or an extension is intentionally fuzzing that data.
#Update 2
I tried Fennec with just jShelter, uBlock Origin, and Cookie AutoDelete (not that I think those last two matter).
Obtained a “randomized fingerprint” result. Success?
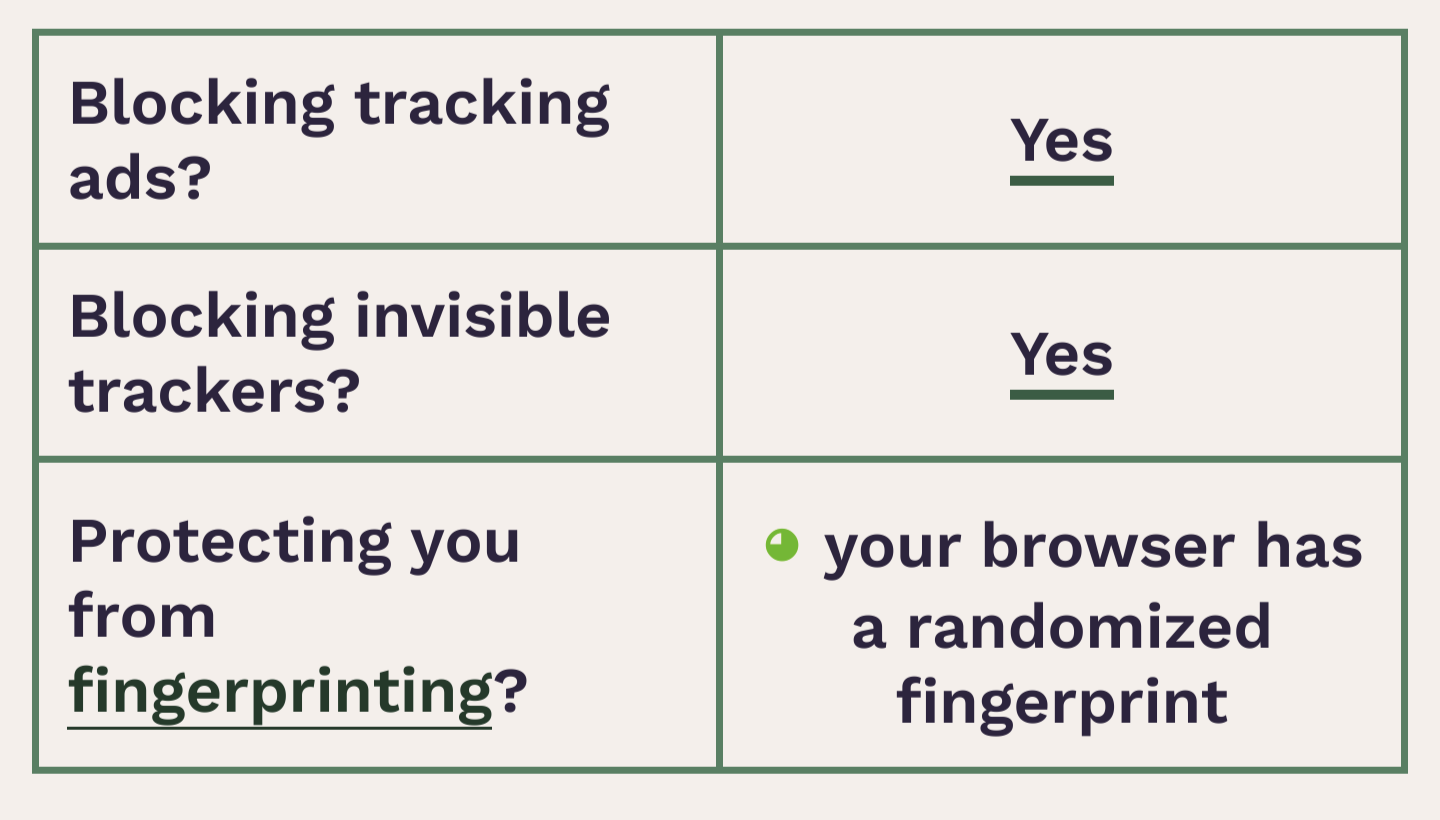
Protip: if your fingerprint changes every 30 seconds, then you’ve defeated their being able to track you with fingerprinting.
Install the Chameleon extension.
The parameter that usually gives me away is the window size, the page suggests its a brittle way of tracking someone since this will usually change from time to time. Not to mention that I’m using a browser that randomizes initial window size,
scroll down and see which fingerprinting parameter gives you away
I’ve done that, and it’s a little of everything. The page doesn’t offer any advice on how to address anything.
The biggest ones are screen size and user agent. User agent can be faked with an extension. I can’t exactly change my screen size.
I don’t know what exactly what I did, but I managed to improve to “nearly unique” in IronFox. I think all I did was install Cookie Autodelete. It’s an extension I’ve used for a long time in Mull, and finally got around to installing it. Then I installed “User-agent Switcher” and chose a Chrome user-agent and now I’m back to “Unique”. 🤔
For the screen size, it’s not actually the screen but the window, which is why tor browser opens in a fixed window size. If you just maximize, even though many use 1080p monitors, your particular settings of your DE give you away (size of bars, window decorations, …)
I’m on mobile.
Ah sorry, missed that, yeah mobile screens are kind of identifying, not sure if any browsers get around that
Cromite manages to randomize it for me in such a way that it’s different every time I check, but I never notice anything myself
The user agent string from each browser
The HTTP ACCEPT headers sent by the browser
Screen resolution and color depth
The Timezone your system is set to
The browser extensions/plugins, like Quicktime, Flash, Java or Acrobat, that are installed in the browser, and the versions of those plugins
The fonts installed on the computer, as reported by Flash or Java.
Whether your browser executes JavaScript scripts
Yes/no information saying whether the browser accepts various kinds of cookies and “super cookies”
A hash of the image generated by canvas fingerprinting
A hash of the image generated by WebGL fingerprinting
Yes/no whether your browser is sending the Do Not Track header
Your system platform (e.g. Win32, Linux x86)
Your system language (e.g. en-US)
Your browser’s touchscreen support
I suspect they’re multiplying all of the 1-in-X probabilities, and if they come up with less than 1-in-8 billion, then they call that unique. If they were actually comparing your values against a hash of previous visitors, then the second time you visit, you’d no longer be unique.
eta: screen size and various hardware measures are probably the lowest probability fingerprints, but they’re all highly correlated - there’s a few million Pixel 7’s out there, but you’ve probably got like 1-in-1000 screen size and a couple other 1-in-500+ hardware, and that would push you to “1-in-billions,” even though there’s millions of people with the same fingerprint.
For me only one parameter was an outlier, so I assumed that you would see something similar…
Stop trying to avoid having a unique fingerprint that’s basically impossible unless you use Mullvad Browser or Tor.
https://github.com/arkenfox/user.js/wiki/3.3-Overrides-[To-RFP-or-Not]#-fingerprinting
Why is it so hard to not be fingerprinted. Surly if everyone generated enough noise then it would be impossible?
Thing is most people just don’t care, and don’t understand it. Also, it turns out it’s really easy to fingerprint people. Your list of installed fonts alone is enough to fingerprint you in many cases, and it’s easy to figure out your entire list of installed fonts with JavaScript.
Add a few more data points like screen size and resolution, user-agent, and you can fingerprint 90% of people. And if that’s not enough, every device—even individual video cards of the same model—renders an HTML canvas differently enough that it’s detectable.
It turns out it’s very hard to not be completely unique when you add all the up.
I feel like it should be a crime to do fingerprinting like this, and to grab and store the browsing habits of every citizen for their whole life, but this is America (for me), and it’s never going to change.
Yeah ik how easy it is i wrote an implementation just to see if i could. But i dont see why browsers cant just lie to websites about absolutly everything. Tell the browser u have fonts u dont u dont have those u dont. Fudge ur window size to a standard set. Put noise into webgl renders. Etc etc. The current approach is to make every device look the same i think the better approach is to make every request look completly different all the time.
“Tell a lie once and it’s a lie, tell a lie a thousand times and it’s a fact. And, when you tell a fact, mix it with a lie and people don’t know what’s true.” - Joseph Stalin
If the trackers cant decern the truth from the lie they cant fingerprint.
Because then you get something that doesn’t work on your browser.
I don’t understand the question. What is “noise”?
The reason it’s so hard is because your browser is telegraphing all sorts of information about your computer to the sites you visit. Some of those things are varying degrees of necessary in order for your browser to function. For example, your time zone is needed in order to show you the correct time for events. There are a hundred of these identifiers. And many nerds like you and me are going to have weird display sizes or use weird browsers or disable certain functions, etc.
If you go to deviceinfo.me, it’s basically a mirror that reflects back at you all the information your browser is feeding it.
Funny enough, not sending info at all can also be used to fingerprint you. That’s why the main strategy for anti-fingerprinting in browsers like TOR is to just send all of the most common info in order to blend in.
Also companies started using “Do Not Track” requests to actually track you.
Im saying to mix in random data into all the information u send. If everyone has a slightly weird display size nobody does etc etc.
Yep, I agree. Not seen any tools that can do that though. I believe Safari has some randomization built in. But fuck Apple.
If you rub sanding paper on your computer you can get rid of fingerprints I hope this helps
Linux x86_64
Hmm. 1 in 6 browsers checked at that site have this value. I’m sure your typical linux user is a little more privacy aware but that’s still an impressive ratio when the overall linux desktop usage is usually pegged between 4% and 5%.
Android shows up as Linux
And scrapers/bots. These make up a staggering amount of web traffic and Linux dominates server land.
Bots are likely going be either special user agents or common ones like Windows
We had to write a classifier for web traffic at a prior employer using known scraper IPs as our training set, and Chrome on Linux got us over 70% of the way there. A sizable number of bots that are just a $5 a month Linux based VPS with selenium and chrome engine.
This website is a lot more specific about the data used for fingerprinting.
It also lets you see whether two seperate visits can be correlated (or if your fingerprint is sufficiently randomized each time).
How long is this supposed to take? I just get this forever.
Turns out jShelter breaks it completely. It runs instantly in DDG browser and same if I disable jShelter.
I get an F- in both cases. 😅
Not a terribly effective test
I get this on Firefox…
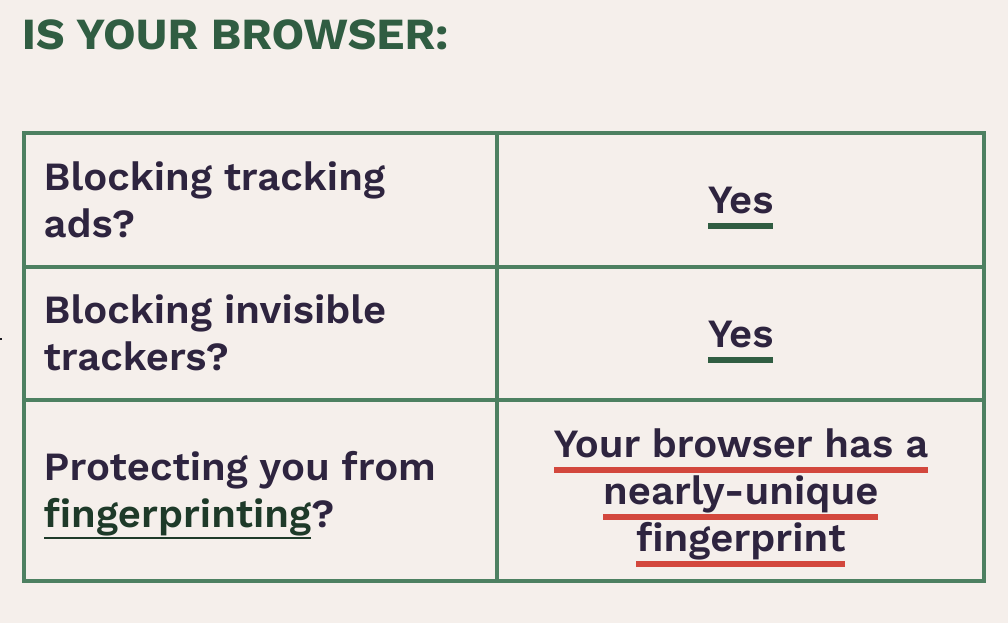
And this on DDG Browser. Both on Android
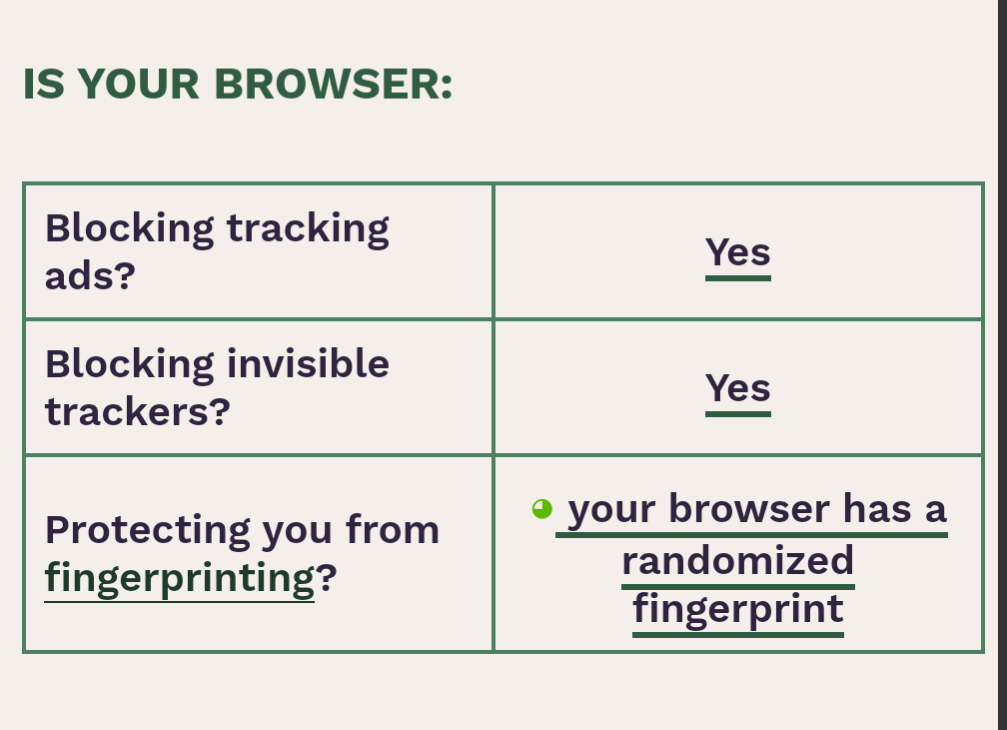
Weird that I get a unique fingerprint in DDG.
Weird, with just jShelter alone, I get “Your browser has a randomized fingerprint” on both desktop and mobile. Firefox browser
Thank you. That’s evidence that mine is not being randomized and is unique and repeatable.
It might be because shelterjs is blocking the script.
why would you need jShelter when you have uBlockOrigin?
isn’t it redundant?
JShelter blocks fingerprinting. uBlock blocks scripts, cookies, and trackers. Trackers are going away, even Google says so, in favor of fingerprinting. Hence why Chrome is moving manifest v3 without third party cookie support. (I hope I got all those facts right.)
An anti-malware Web browser extension to mitigate potential threats from JavaScript, including fingerprinting, tracking, and data collection!
what if JavaScript is already disabled (by your browser or by uBlock)?
I’ve never seen it not be unique. You can get pretty close though.
I got into be random in Fennec. That’s good. A unique, random fingerprint is probably as good as hiding in the crowd. Maybe. I dunno.
I feel like a lot of people on Lemmy will have unique fingerprints due to using uncommon operating systems, browsers, and extensions.










